Disabling Unauthenticated Binds in Active Directory
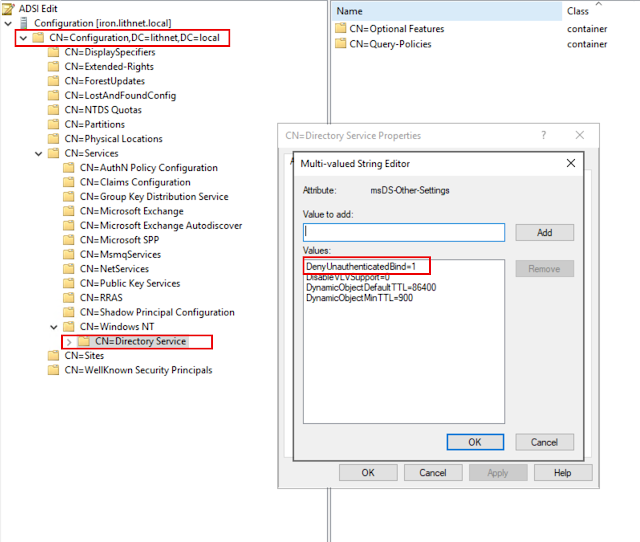
In January last year, I wrote a (long) post detailing a curious behavior I stumbled across in Active Directory's LDAP interface. By providing a username, but leaving the password blank, you were authenticated as an 'anonymous user'. This is technically a valid LDAP behavior, and is known as an 'unauthenticated bind'. However it's obscure, not well known, and the cause of many security vulnerabilities . To recap, the LDAP RFC states the following; 5.1.2. Unauthenticated Authentication Mechanism of Simple Bind An LDAP client may use the unauthenticated authentication mechanism of the simple Bind method to establish an anonymous authorization state by sending a Bind request with a name value (a distinguished name in LDAP string form [ RFC4514 ] of non-zero length) and specifying the simple authentication choice containing a password value of zero length The RFC goes on to acknowledge this is an objectively terrible idea, and recommends that servers ...