Getting started with Lithnet Password Protection - Part 1 - Blocking compromised passwords with the 'Have I Been Pwned?' password list
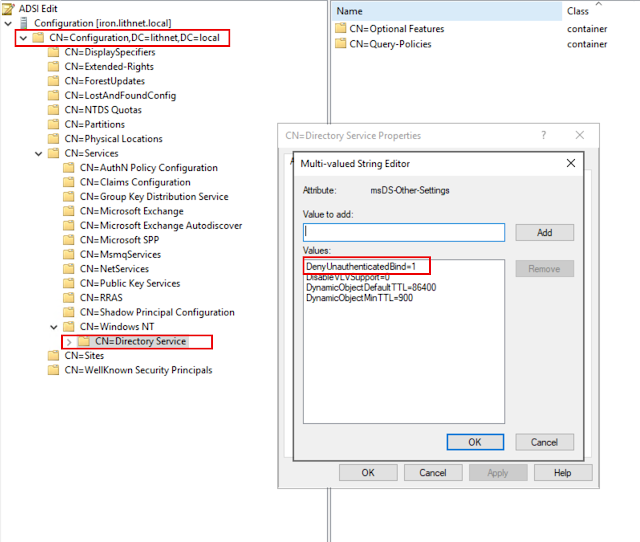
NOTE: Please visit docs.lithnet.io for the most up-to-date setup instructions In this guide, we will look at how to set up Lithnet Password Protection for Active Directory (LPP) from scratch. We'll configure a basic password policy, and integrate the haveibeenpwned.com pwned password data set to prevent users from changing their password to one that is known to be compromised. This guide will focus on testing in an Active Directory domain, by installing the agent on a domain controller. However, for testing purposes, you can install the agent on a member server or workstation. The only difference is you'll need to test using local accounts, rather than domain accounts. Prerequisites You'll need to be using an x64 version of windows. LPP is a x64-only application. You must have local administrator rights on the server you want to install the agent on. For domain controllers, this means being a member of the Domain Admins group. Download the latest version of the N...